Hi everyone! As part of making Airtable apps safer for our customers, we’re rolling out tighter security restrictions for our marketplace apps, along with a network access option for Enterprise administrators.
Apps are a powerful way to extend Airtable that gives superpowers to teams and companies of all sizes. We’re continually looking to make apps more secure and transparent to users, so we’re taking the first step to tighten app security and give users more visibility over how apps access their data. Our hope is that this long-term commitment to security and transparency will make Airtable a more valuable platform for developers and users alike.
On February 10, 2021, we’ll start to enforce several browser-based security settings for any apps installed from the marketplace, including existing apps already installed in bases. The enforcement uses Content Security Policy headers (CSP), which are an industry-established standard for browser security. As part of this enforcement, we’ll use browser directives to prevent apps from using insecure JavaScript and browser patterns such as using eval() or running externally hosted scripts.
We’ve tested all apps currently in the marketplace, and they will all continue to work following this change. Note that these enforcements will not affect any custom apps you create and install yourself from outside of the marketplace, although this may be subject to change – with plenty of notice! – in the future.
“Network access” option and upcoming Enterprise control
We’ll soon start to differentiate marketplace apps that require “network access” from those that don’t, and make this explicit for our end users. Today, some apps need to communicate with external services to work – for example, the “SendGrid” app would need “network access” to be able to communicate with the SendGrid API to send emails. Other apps only need information that’s already in the Airtable base itself, and therefore don’t need “network access” – for example, the “Chart” app.
Though emailing via SendGrid may be innocuous, a malicious app with “network access” could theoretically send data from the base back to the developer’s own servers. We carefully review apps that are published to the marketplace to protect against this sort of malicious code, but with this new enforcement of CSP headers, we can go even further.
Going forward, we will allow apps to declare that they don’t require “network access,” and our app platform will apply a corresponding Content Security Policy setting to ensure that this is enforced by the browser when users use the app. We’ll have a visual indicator in our marketplace for these apps, to communicate their additional level of security to users.
For Enterprise users, their administrators will soon be able to allow or deny apps based on whether they require network access. We will also use feedback from this Enterprise control to inform our long term roadmap for a potential app permission control system for all users.
New developer tool to prepare for publishing to the marketplace
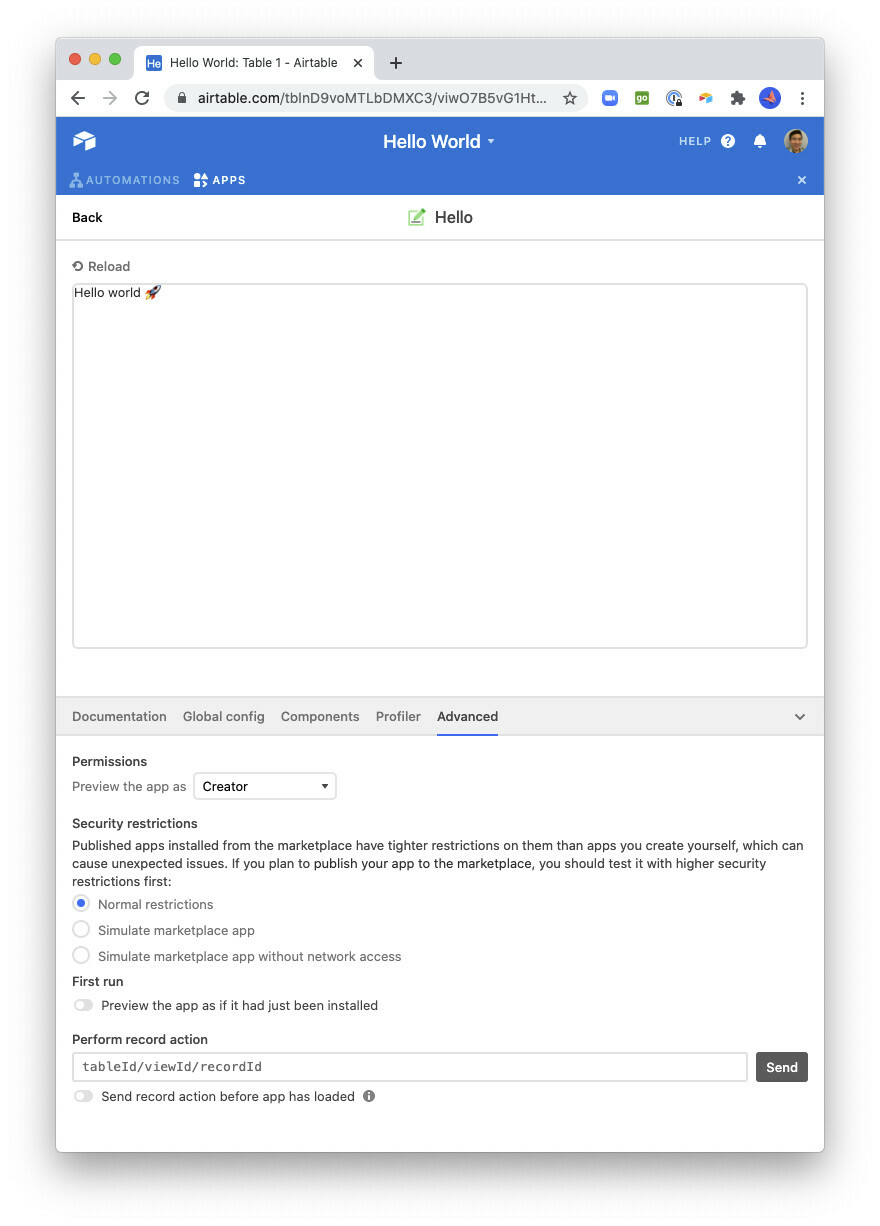
If you’re planning to publish your app to the marketplace, we have a new interface in the development workflow to test out the higher security restrictions first. Your app needs to at least work on the “Simulate marketplace app” setting. If it doesn’t require access to any external services or resources, then making it work on the “Simulate marketplace app without network” setting will ensure that it reaches the widest possible audience.
One important note: many marketplace apps today rely on communicating with 3rd-party “token validation” services in order to monetize. These apps will need to declare as “requires network access” to continue working as intended in our marketplace, until we can provide monetization support directly in the Airtable platform. In the meantime, we deeply value any feedback and examples of how you’d like to see first-class monetization work in the future.
FAQ
If my app is already in the marketplace, what will happen to it?
We’ve determined which currently-published apps already meet the bar for “not requiring network access,” and will be classifying them as such. If you’d like to change the network behavior for your published app, please see the next question for more details.
If I publish my app with one network behavior, but then want to submit an update that changes this, will I be able to?
If your app changes the network behavior from “requires network access” to “does not require network access”, mention that change in your publish notes, and we’ll work with you to get the correct status applied.
The reverse direction of switching from “does not require network access” to “requires network access” introduces a risk, as this would break user expectations for existing installed apps, so we will initially disallow it. If you have a use case that depends on the option to do that, please let us know in the comments below.
Behavior overview
| Marketplace apps before February 2021; all custom apps (currently unaffected) | Marketplace apps after February 2021 using security restriction, with network | Marketplace apps after February 2021 using security restriction, without network |
|---|---|---|
| Content Security Policy headers are not enforced. | Content Security Policy headers are enforced | Content Security Policy headers are enforced |
| Insecure JavaScript usage such as eval() is flagged in the marketplace review process. Running externally hosted scripts are allowed. | Insecure JavaScript usage such as eval() is restricted by the browser. Running externally hosted scripts are not allowed. | Insecure JavaScript usage such as eval() is restricted by the browser. Running externally hosted scripts are not allowed. |
| Network access is allowed. External resources (media, fonts, stylesheets, etc.) can be loaded over the network. | Network access is allowed. External resources (media, fonts, stylesheets, etc.) can be loaded over the network. | Network access is restricted by the browser. External resources (media, fonts, stylesheets, etc.) cannot be loaded by the browser. |
| Enterprise administrators can allow or deny all marketplace apps. | Enterprise administrators can allow all marketplace apps, just marketplace apps without network, or no marketplace apps. | Enterprise administrators can allow all marketplace apps, just marketplace apps without network, or no marketplace apps. |


