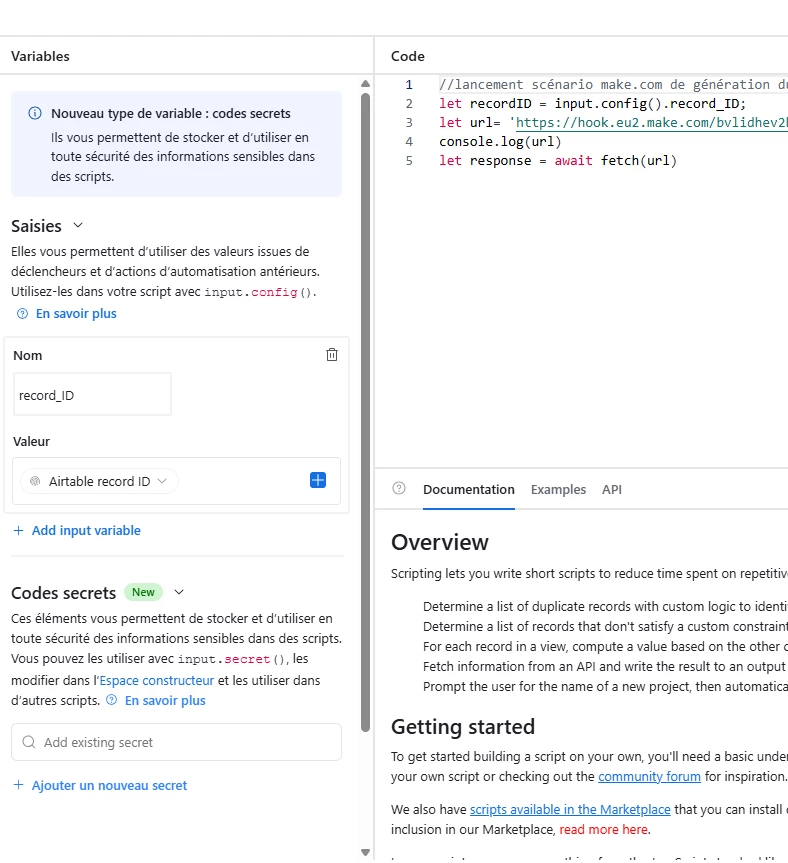
I have an automation that invokes an API taht requires authentication credentials. What is the best way to store those credentials so they cannot be read outside of the automation? Does the input.config do anything to obfuscate them?
How to safely store environment variables in automations
 +1
+1Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.