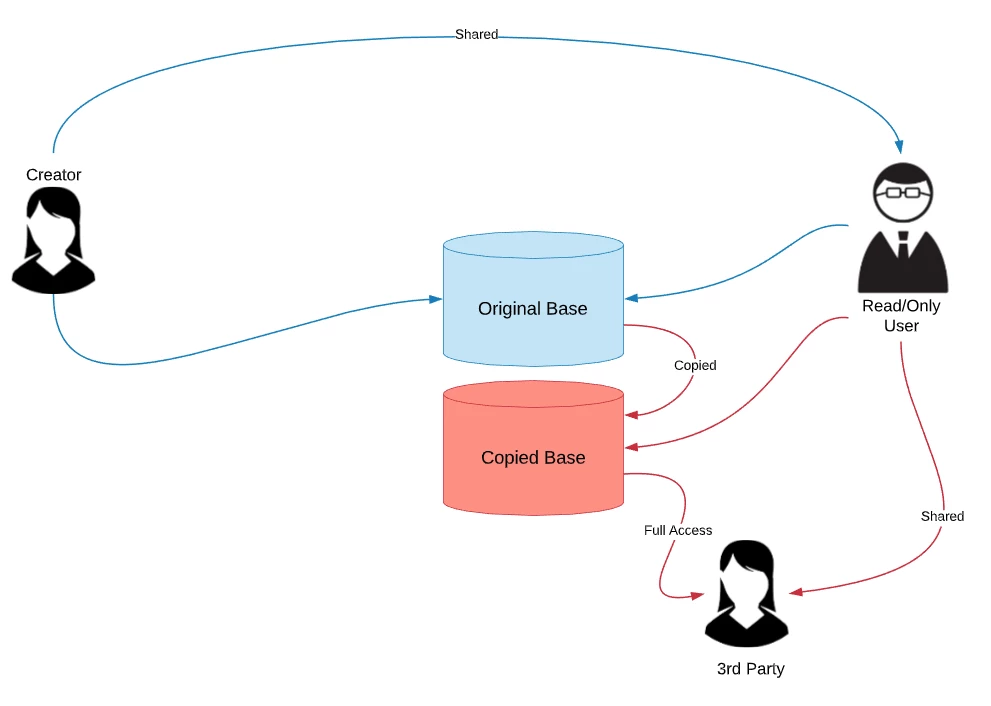
This thread made me realize that we should probably have an option to PREVENT collaborators (particularly read-only collaborators) from being able to easily duplicate an entire base.
When we share read-only links to bases or views, we have that option that we can uncheck that says: “Allow viewers to copy the data in this base” or “Allow viewers to copy data out of this view”.
But it would be nice if we had that same feature for collaborators.